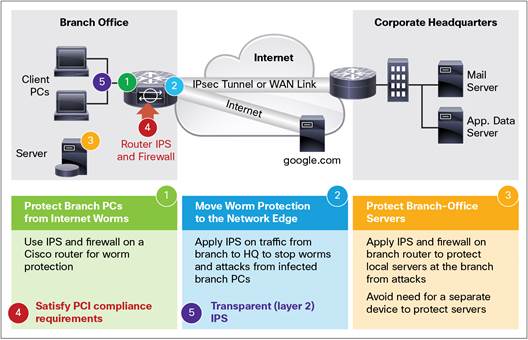
CVE-2022-20699, CVE-2022-20700, CVE-2022-20708: Critical Flaws in Cisco Small Business RV Series Routers - Blog | Tenable®

Cisco Router Vulnerability Puts Network Segmentation at Risk | Data Center Knowledge | News and analysis for the data center industry

US, UK security agencies warn of APT28 hackers exploiting known Cisco vulnerability, issue mitigation action - Industrial Cyber

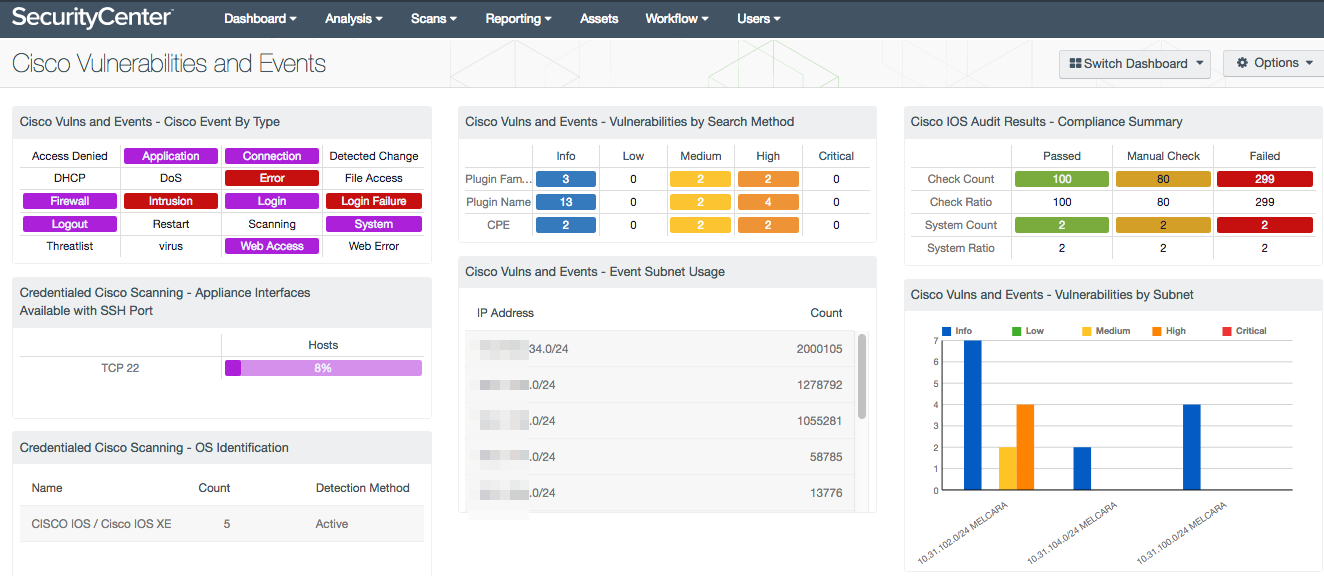
Nessus Scanning Cisco Switches| Nessus Vulnerability Scanner | Nessus Tutorial | Nessus Step by Step - YouTube